
Meta Platforms on Friday disclosed that it had identified over 400 malicious apps on Android and iOS that it said targeted online users with the goal of stealing their Facebook login information.
“These apps were listed on the Google Play Store and Apple’s App Store and disguised as photo editors, games, VPN services, business apps, and other utilities to trick people into downloading them,” the social media behemoth said in a report shared with The Hacker News.
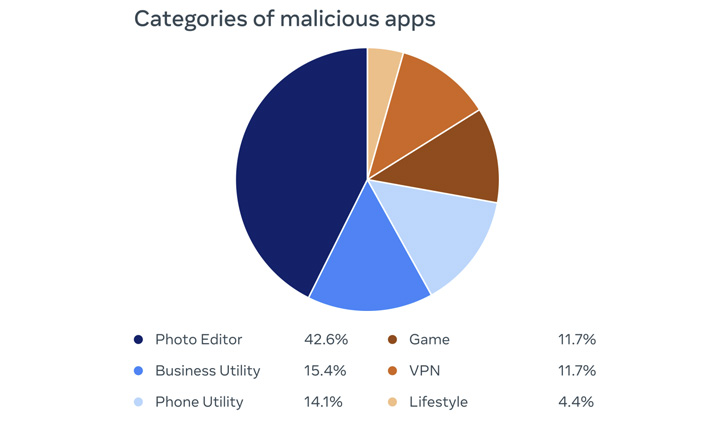
42.6% of the rogue apps were photo editors, followed by business utilities (15.4%), phone utilities (14.1%), games (11.7%), VPNs (11.7%), and lifestyle apps (4.4%). Interestingly, a majority of the iOS apps posed as ads manager tools for Meta and its Facebook subsidiary.
Besides concealing its malicious nature as a set of seemingly harmless apps, the operators of the scheme also published fake reviews that were designed to offset the negative reviews left by users who may have previously downloaded the apps.
The apps ultimately functioned as a means to steal the credentials entered by users by displaying a “Login With Facebook” prompt.
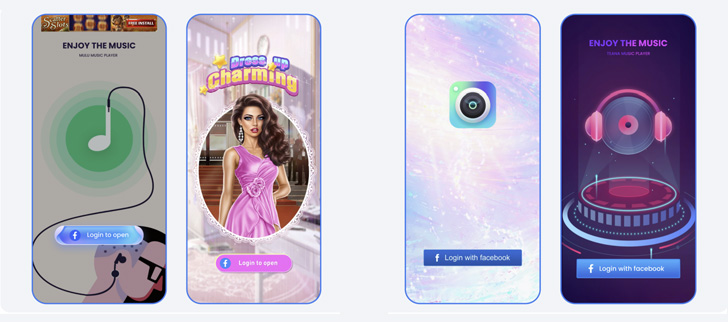
“If the login information is stolen, attackers could potentially gain full access to a person’s account and do things like message their friends or access private information,” the company said.
All the apps in question have been taken down from both app stores. The list of 402 apps (355 Android and 47 iOS apps) can be accessed here.
As always with apps like these, it’s essential to exercise caution before downloading apps and granting access to Facebook to access the promised functionality. This includes scrutinizing app permissions and reviews, and also verifying the authenticity of the app developers.
The disclosure also comes as Meta-owned WhatsApp filed a lawsuit against three companies based in China and Taiwan for allegedly misleading over a million users into compromising their own accounts by distributing bogus versions of the messaging app.
Source – https://thehackernews.com/2022/10/facebook-detects-400-android-and-ios.html?m=1
